Scammers using deepfake nude images to demand money from victims in Singapore
Instagram account of the scammer "Janice". She sent John a photo with his face on the naked body of a man. PHOTO: KYLEEN CABAEL
Kyleen Cabael
Jun 29, 2024
SINGAPORE - A few days after John (not his real name) connected with a woman on the dating app OkCupid, he received a message from a friend who said someone had sent him a photo purportedly of John in the nude.
John, 21, said he knew it was the woman he met on the dating app in June 2024.
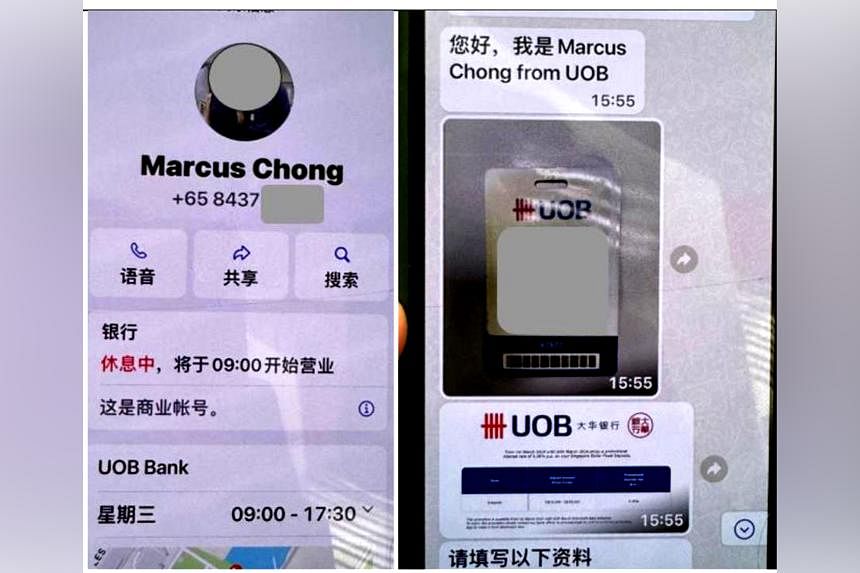
Janice had insisted they chat via video call on Telegram. Hours later, she sent him a photo with his face on the naked body of a man.
She threatened to distribute the photo to his friends on various social media platforms unless he agreed to transfer $1,000 to a bank account.
John told The Straits Times he never sent her a picture, let alone a nude shot. They had only one video chat.
That image turned out to be a deepfake, with scammers using face-swopping artificial intelligence (AI) technology to transpose John’s face on another body.
ST has learnt that at least four men have been targeted by scammers in what has been coined “deepfake sexploitation”.
John refused to pay, but others did, with one victim squeezed by the scammers for repeated payments.
Two of the men were approached while on OkCupid, which charges subscribers between $10.89 and $32.46 for tiered membership.
Janice’s OkCupid profile showed that she resided in Singapore. She claimed to be a 21-year-old half-Japanese who enjoyed eating sushi.
“Her profile wasn’t anything out of the ordinary, and it took a day for us to get matched,” John said, adding that they were matched on June 1.
He then struck up a conversation with her through the app’s message function. They hit it off and exchanged Telegram and Instagram contacts.
Four days later, she requested a video call and he agreed.
“She looked a bit different from her profile picture, but I didn’t think anything of it. But it was weird how insistent she was to call,” he said, adding that she did not sound Singaporean.
“She kept on saying provocative stuff like ‘I want to do it now’ towards the end of the call,” said John.
ST ILLUSTRATION: MIEL
He decided they were not a good match and ended the call. A few hours later, John received the message from his friend about the deepfake nude image. Janice’s threat followed shortly after that.
Although shocked, John ignored the threat since he knew his conscience was clear. He also searched for advice online. “I learnt that scammers usually do not carry out the threat, because they are only after the money,” he said.
John saw that Janice had deleted her OkCupid account before he paused his own.
On the same day John was blackmailed by Janice, he received a message from his friend Sam (not his real name), also 21. Both men are full-time national servicemen.
Sam wanted to know if John knew Janice, because he noticed that John followed her Instagram account. It turned out that Sam was a victim too.
He met Janice on OkCupid around the same time as John. She did the same thing with Sam – chats on the app and then a video call on Telegram.
The threat was also similar, except she wanted him to pay $2,000.
Sam feared that nobody would believe him and paid up.
Joel (not his real name), 25, also caved in.
In his case, the scammers squeezed him for a total of $2,200, after initially demanding $700.
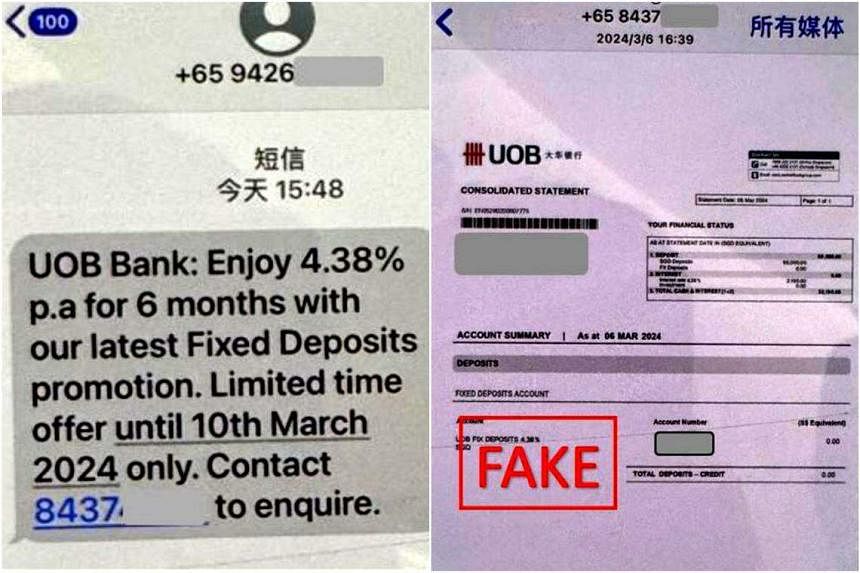
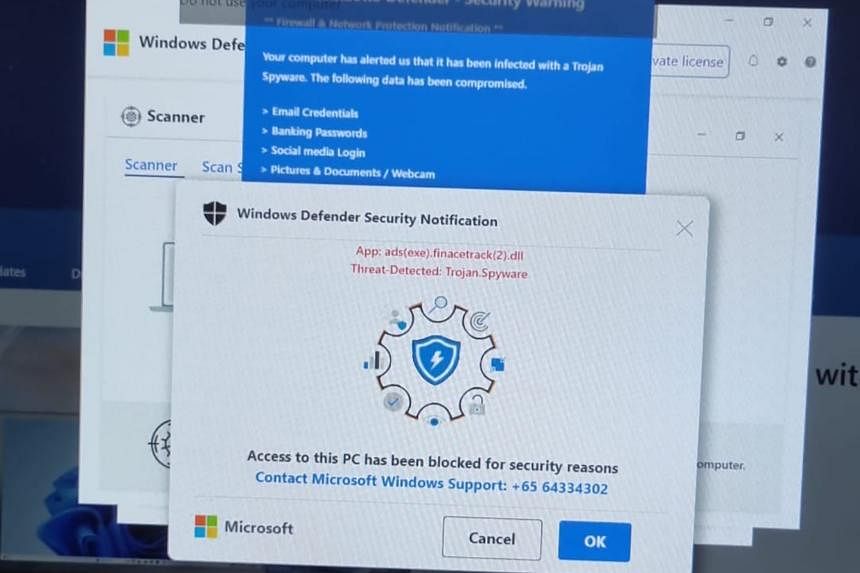
In August 2023, Joel clicked on a phishing e-mail, which he thought was a response to a scholarship he had applied for. He was redirected to a website that scanned his face.
A few days later, he received an explicit video of himself from an unknown user. He was horrified, as he realised it was a deepfake. The scammers threatened to distribute the video to his friends unless he paid them $700.
Joel said: “I was scared because they said they had the contacts of my relatives, friends and colleagues. The video looked quite realistic, too.”
He paid the scammers the money and pleaded with them to delete the video. They demanded more money and Joel paid $2,200 over three transactions before he sought help.
“I realised there was no stopping, so I talked to my brother, who suggested I report the incident to the police,” said Joel.
Deepfake sextortion
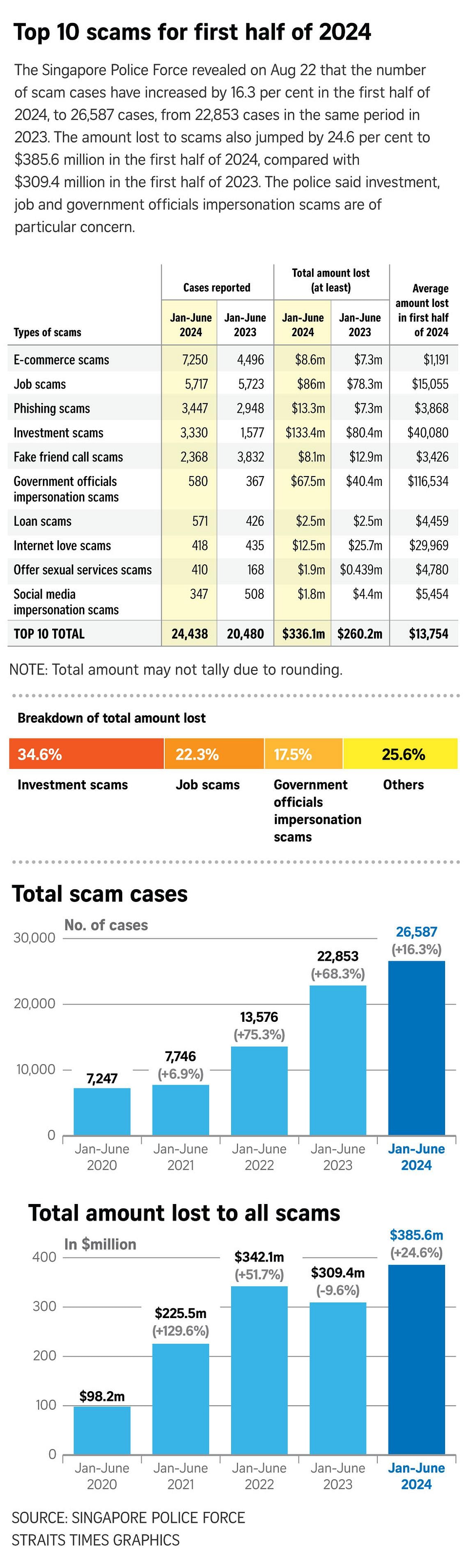
The number of scam cases in Singapore hit a record high in 2023,
with over 46,000 cases reported. That year, scam victims lost a total of $651.8 million.
Of the top 10 scam types reported by the Singapore Police Force in 2023, internet love scams ranked fourth, with victims losing $39.8 million.
Victims of internet love scams are tricked into sending money or gifts to scammers, hiding behind fake social media profiles. The scammers usually act affectionate to gain the trust of victims before asking for money.
While the police have figures for most scams, they do not track the number of deepfake-related scams.
In a written reply to a parliamentary question, Home Affairs and Law Minister K. Shanmugam said in April 2024 that there have been some reports where the complainants alleged that deepfake techniques were used by the scammers.
But he added that the number is not high.
Deepfake sextortion is a new phenomenon, but it has made headlines overseas.
In Britain in April 2024, a man was blackmailed with a deepfaked video of himself masturbating. He suspected that the scammer had obtained his contacts and camera gallery after he picked up a phone call from an unknown number.
Mr Leonardo Hutabarat, head of solutions engineering for Asia-Pacific and Japan at cyber-security firm LogRhythm, said: “As the public becomes more aware of AI technology and deepfake software, the use of deepfake scams for schemes like sextortion is likely to rise, especially in Asia.”
Some of the scammers are operating out of centres established in Cambodia. Many of the people carrying out the scams were lured with false job premises but forced to run online scam, said Mr Hutabarat.
He said the Indian government was reported to have
rescued 250 of its citizens from Cambodia in April 2024 who were forced to work at the centres and carry out scams, including sextortion.
He added: “These scams typically target individuals seeking romantic relationships and can cause significant damage to victims.”
Mr Hutabarat said scammers have also used deepfake tools to clone voices of friends, family members or authority figures to make urgent requests for money transfers or sensitive information.
He said: “The fake audio sounds extremely realistic, making it hard to detect.”
Cyber threats
The Cyber Security Agency of Singapore (CSA) said the rise of generative AI (gen AI), which matured significantly in 2023, can increase productivity by automating repetitive tasks and allow for more efficient creation processes.
However, it also brings a new dimension to cyber threats, such as the ability to create deepfakes.
“As user-friendly gen AI tools and tutorials become increasingly available, anyone who is moderately tech-savvy can get started and produce decent deepfakes within a relatively short period of time.
“With such lowered barriers to entry, we expect to see an increase in the creation and usage of deepfakes, which can be used for various malicious purposes,” said a spokesperson for the agency.
In February 2024, CSA said a finance worker at a multinational firm in the Asia-Pacific region was tricked into transferring US$25 million ($34 million) to scammers who used deepfake technology to pose as the company’s chief financial officer in a video conference call.
Mr Hutabarat said some companies are even offering services called Deepfakes-as-a-Service, where customers can obtain professional deepfake content for a fee.
CSA, which provides an advisory on how to detect deepfakes on its website, said those who have been subjected to a deepfake scam should alert the police and notify any organisation involved.
“Netizens who have been targeted are advised not to pay scammers, as paying them does not guarantee that they will stop,” CSA added.
Mr Hutabarat said it is essential for the victim to alert the police so that the scammer is held accountable and the explicit images are not shared.
He said: “Gathering evidence is crucial for any investigation, so it’s important to keep a record of all communications and ensure that no malicious software has been installed on the victim’s system.”
Of the four victims ST contacted, only Joel has filed a police report.
“I realised the scammer will never stop. I am just a student, I could not afford to lose so much money,” he said, adding that he wished he had spoken to his brother sooner.
“I feel like I was too naive and wasn’t cautious. I should have noticed it was a fake e-mail,” Joel added.
Dr Annabelle Chow, clinical psychologist at Annabelle Psychology, said that victims are often anxious and end up paying the scammers despite knowing the images are fake.
“There’s a lot of insecurity from the victim because the image can seem very realistic. Other people might not be able to tell real from fake. There will also always be an element of doubt or judgment from someone who views the fake image,” she said.