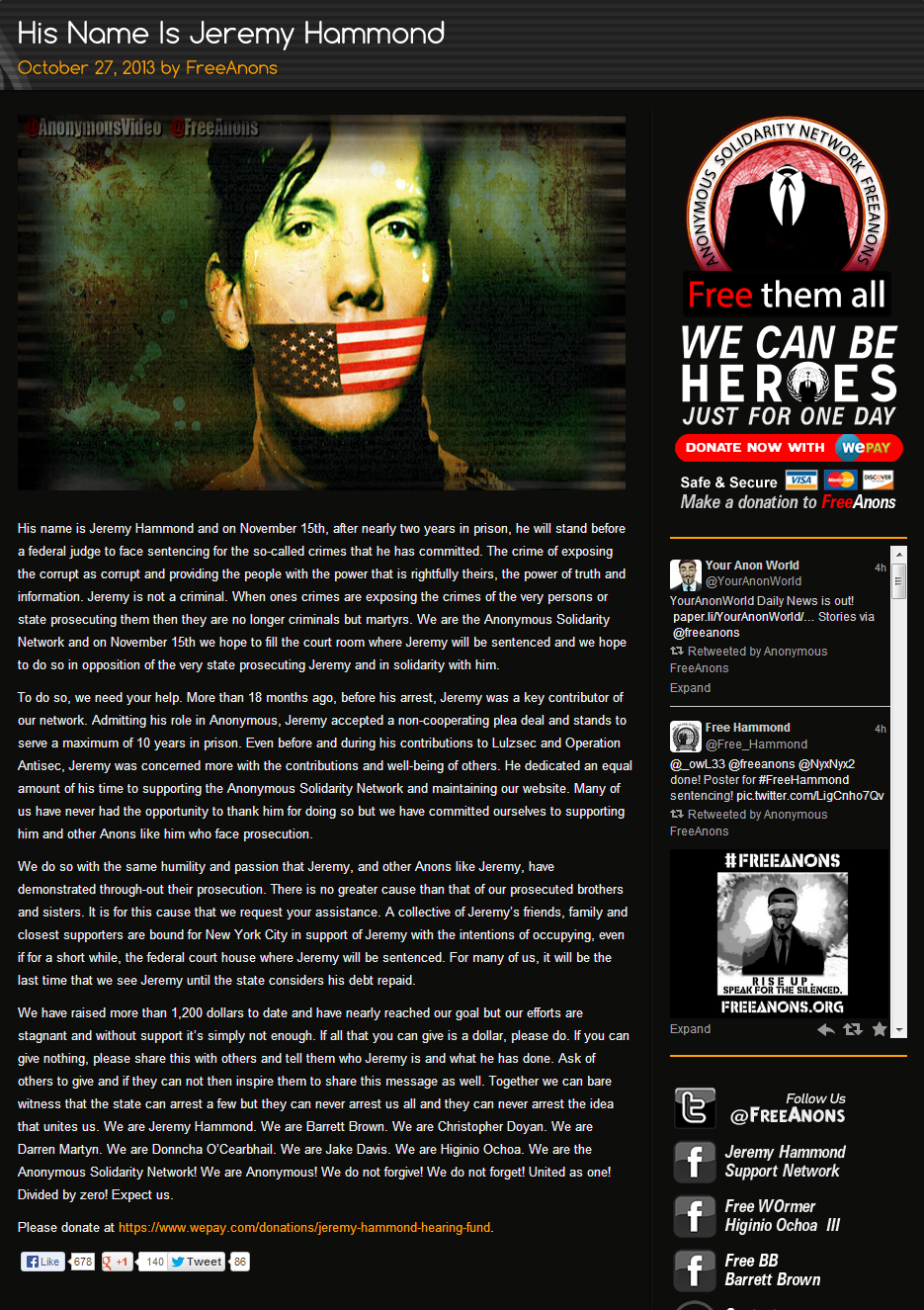
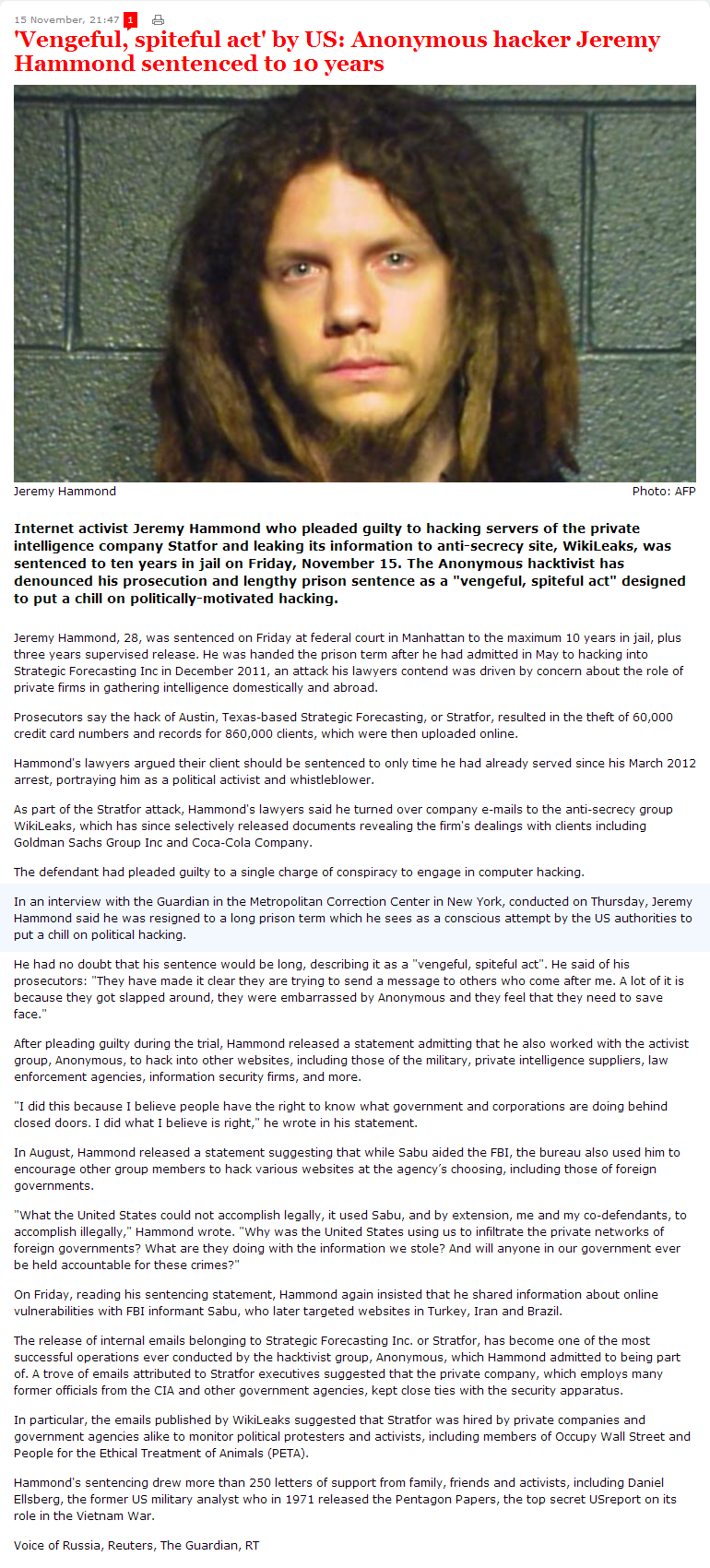
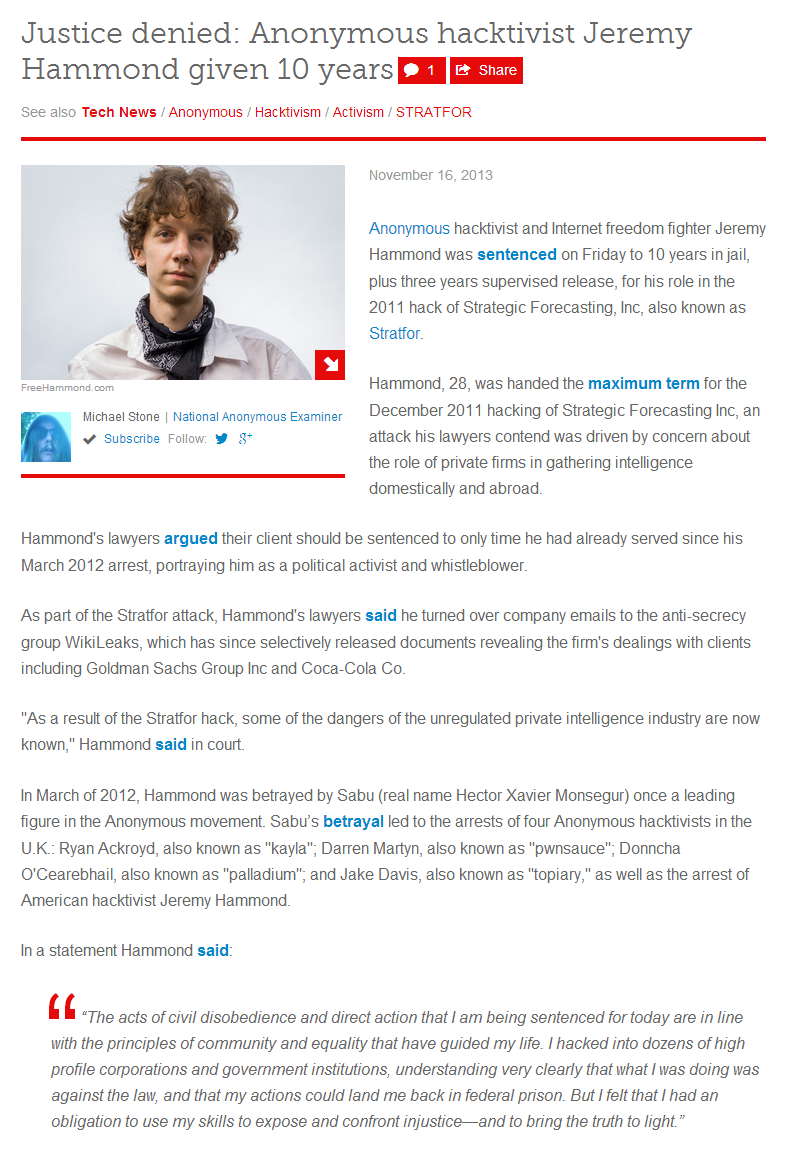
BLOG: Anonymous targeting Asian government sites
Wade Williamson | Nov. 11, 2013
Guy Fawkes Day was November 5th, and a variety of loosely affiliated movements from Occupy to Anonymous joined to commemorate the day with a Million Mask March. However, it seems that Anonymous or at least Anonymous affiliated hackers in Asia decided to get an early start on the festivities with a variety of attacks against government websites in Australia, Singapore, and the Philippines.
Thus far, these attacks all bear the unmistakable signs of hacktivism, in that the compromised sites were defaced with political messages. Obviously, these sorts of attacks are nothing new, and we have been seeing a bit of their resurgence in the past few months. Prior to this action from Anonymous, the Syrian Electronic Army or SEA had claimed responsibility for a string of attacks targeting large news media organizations ranging from the New York Times to Twitter.
Whenever one of these attacks makes the news, it always seems to spur questions about how such a thing can continue to happen. I wanted to briefly share some of the more common tactics we are seeing against legitimate websites.
Direct Attack
First, it's important to realize that websites, and more specifically web servers, are very common targets for attackers. If the website accepts input from an end-user, that site can be subject to a variety of injection techniques that can allow an attacker to compromise data that the website serves, or ultimately compromise the server itself. These attacks will typically exploit a weakness in the way that the website or application validates a user's input, which allows an attacker to send specially crafted input to compromise the webserver or application. These attacks are extremely common, and are generally mitigated through a combination of IPS to detection injection attacks, web-application firewalling to detect specific attacks against web applications, vulnerability testing of websites, and training to ensure secure coding and web development practices.
Password Compromise
Ultimately, people manage websites, and those people will have passwords to authenticate themselves when managing the site. If an attacker can compromise those credentials, then the attacker gains all the privileges and access of the administrator. This technique was heavily utilized earlier in the year when the SEA was able to steal Twitter credentials for news organizations and was able to send out fake news updates that caused significant movement in financial markets.
This approach can somewhat bridge the gap between hacktivism and the more advanced threats or APTs. To steal a valid user's credentials, attackers will send targeted phishing emails in order to lure the user into entering their credentials into the attacker's website or to deliver malware to the target that will steal the user's password from the local machine. This approach includes some of the basics of an APT, but ultimately the goal is still to gain notoriety for the attacker. Mitigating these attacks requires a complete approach to cybersecurity capable of blocking all types of malicious traffic and content ranging from drive-by downloads, exploits and malware to command and control traffic and malicious URLs, as well as proactive testing of any unknown files or traffic to expose hidden threats. Additionally, end-user training can help users learn to recognize phishing attempts, and two-factor authentication should be implemented to protect web resources from simple password compromises.
DNS Hijack and Redirect
Stealing passwords can be useful for an attacker in a variety of ways. The SEA attacks against the New York Times and variety of other sites provided a stark case in point earlier this year. In that case, instead of stealing passwords from the New York Times directly, the attackers targeted the DNS registrar that the Times uses for its websites. In short, the attackers didn't really attack the New York Times directly at all - they simply broke in to Melbourne IT (the DNS registrar for the New York Times) and changed the DNS record for nytimes.com to point to an IP address in Syria.
An attack such as this is obviously hard to control from an IT perspective simply because the attack never directly touches the intended target. That underscores the importance of choosing a registrar that asks thorough, pointed questions about how security is handled by the vendor. Many registrars will offer additional safeguards and locks that make it far more difficult and time-consuming to make any domain level changes to an account, although not all registrars do this.
Ultimately, there are plenty of methods that can be used by hacktivists to compromise a site and its data. Hacktivism season seems once again in full swing, so it's crucial to know what you're up against and safeguard your data as much as possible.
Wade Williamson is Senior Security Analyst at Palo Alto Networks.