Coronavirus Scam Alert: Watch Out For These Risky COVID-19 Websites And Emails

Thomas BrewsterForbes Staff
Cybersecurity
Associate editor at Forbes, covering cybercrime, privacy, security and surveillance.

Computer viruses are likely to spread as malicious hackers make the most of the COVID-19 panic. ... [+]
SOPA IMAGES/LIGHTROCKET VIA GETTY IMAGES
Cybercriminals and nation state-sponsored spies didn't take long to catch onto the coronavirus panic. Research released Thursday shows crooks and snoops have been rapidly registering vast numbers of potentially-malicious websites and sending out masses of scam emails as they try to make money from the pandemic.
A report from cybersecurity company Recorded Future noted a significant rise in website registrations related to the COVID-19 virus, some of which it believes are being used to either pilfer information from recipients or infect them with malware.
Lindsay Kaye, director of operation outcomes at Recorded Future, specifically called out the following domains as potentially dangerous:
Forbes also had Bernardo Quintero, founder of the Google-owned malware repository and anti-virus testing service VirusTotal, take a look at the domains reported by Recorded Future. He said the following websites also showed signs of malicious behavior, as they’re being detected by anti-virus software:
Today In: Cybersecurity
A significant number of additional coronavirus-related domains have been registered in recent days, and whilst they hadn’t yet been linked to criminal activity, they may do in the coming weeks, said Kaye.
There are, for instance, domains registered that appear to come from the Centers for Disease Control and Prevention (CDC), when in fact they’re from dangerous spammers. Researchers have already found one malware that was spread via the legitimate-looking email address CDC-Covid19@cdc[.]gov. And, as previously reported, there is at least one malicious coronavirus map that secretly installs malware that can steal information from victim PCs.
“It is advisable to treat all emails regarding the COVID-19 outbreak with caution,” wrote Recorded Future.
Phishing email examples
Cybersecurity company FireEye provided Forbes with a handful of example spam emails. Often such scams will ask you to click on a link or attachment so that you can get more information about protecting yourself from coronavirus.
Again, if you see anything that looks like they following, it’s wise to close and delete the email, and not click on links or attachments.
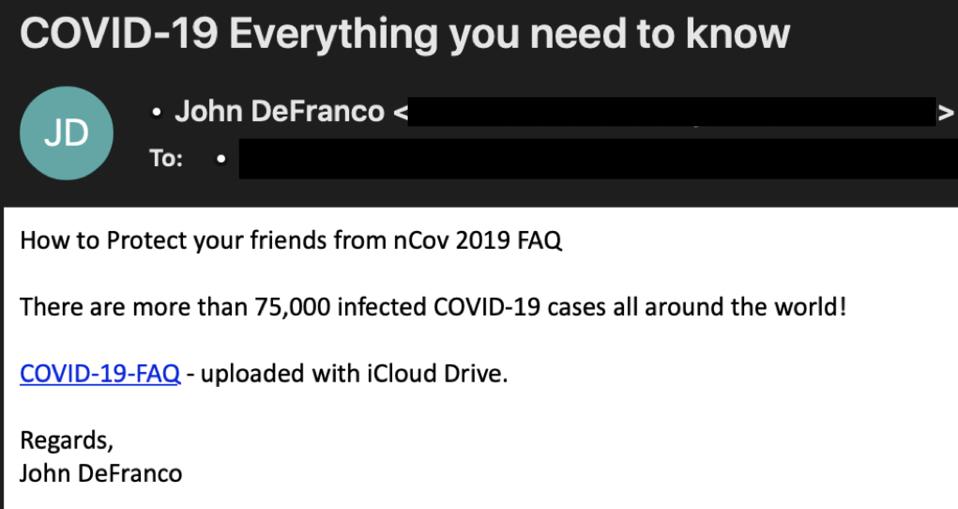
A criminal phishing email seeking to take advantage of the coronavirus pandemic.
FIREEYE
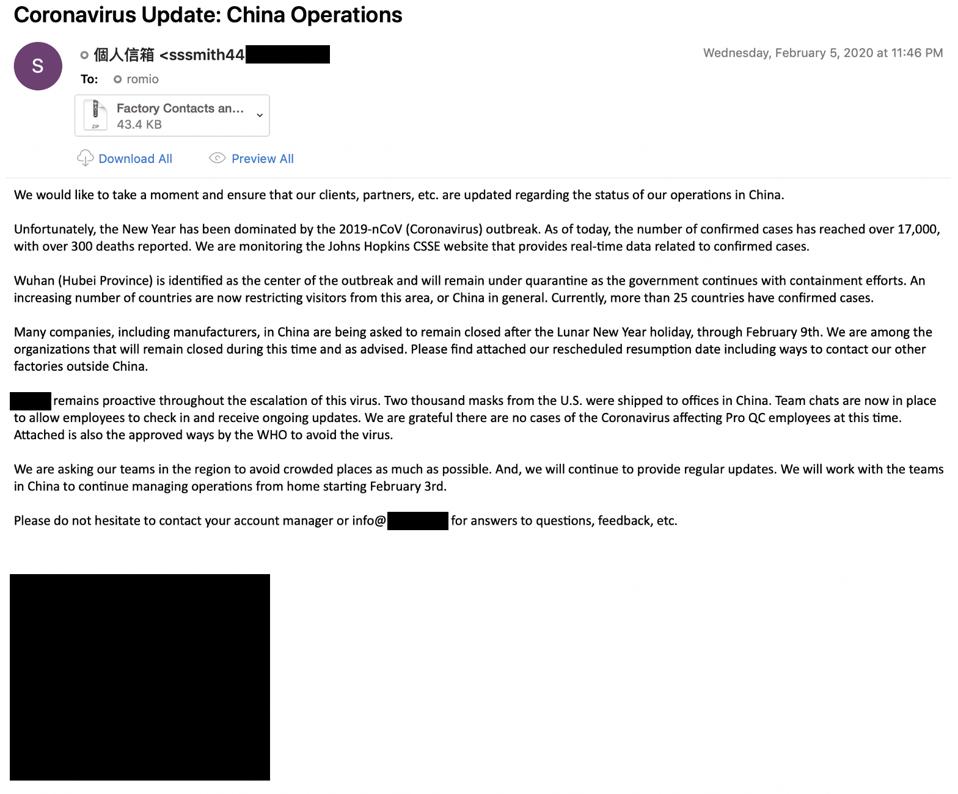
Another malicious phishing email seeking to take advantage of the coronavirus panic.
FIREEYE
FireEye also looked at some of the attachments being sent in COVID-19 phishing emails. If you’ve downloaded something similar to this, run your antivirus and any other security tools that can help you check for infection.
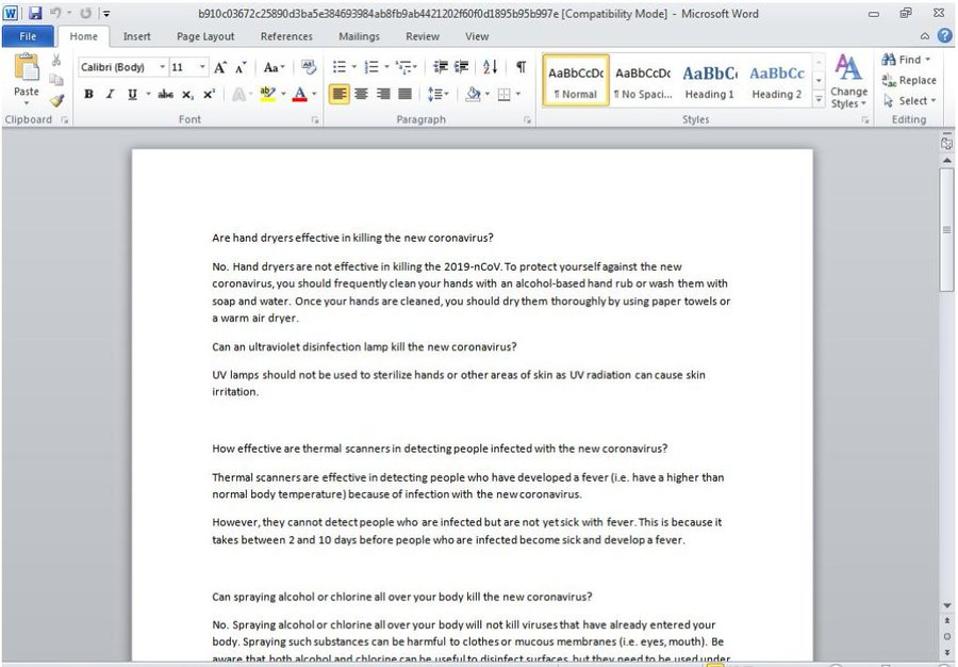
A "lure" document that FireEye believes a Chinese group of hackers used to try to infect targets in ... [+]
FIREEYE
Government spies are taking advantage of coronavirus
It’s not just opportunistic scammers who’re making the most out of coronavirus. Espionage groups associated with China, North Korea and Russia have been seen sending out spear phishing emails trying to find routes onto business networks.
Entire industries are being targeted. In February, cybersecurity company Proofpoint noted Coronavirus-themed email attacks tried to play on concerns about disruptions to global shipping. The hackers behind the operation were “exclusively targeting industries that are particularly susceptible to shipping disruptions including manufacturing, industrial, finance, transportation, pharmaceutical, and cosmetic companies.”
In late February and early March, FireEye suspected a group of Chinese hackers had sent malware-laden documents to targets in Vietnam, the Philippines and Taiwan.
The documents included legitimate statements by political leaders and advice from official sources, but hidden underneath was data-slurping spyware. As reported by ForbesThursday, a Chinese hacking crew has been linked to coronavirus-led attacks on Mongolians.
FireEye also reported that an espionage group called TEMP.Armageddon, which “acts in support of Russian interests,” sent a spear phishing email with a malicious, coronavirus-themed document to Ukrainians. And the company’s researchers said they’d seen South Korea NGO targeted with a Korean-language lure entitled “Coronavirus Correspondence.” Though they’re still probing the attack, the analysts have already noted some similarities to previously-seen North Korean hacks.
If you’re a potential target for cybercrime or international spies - which means you are a human being who uses the internet - be careful with what emails are trying to stoke the fire of your coronavirus fears.

Thomas BrewsterForbes Staff
Cybersecurity
Associate editor at Forbes, covering cybercrime, privacy, security and surveillance.

Computer viruses are likely to spread as malicious hackers make the most of the COVID-19 panic. ... [+]
SOPA IMAGES/LIGHTROCKET VIA GETTY IMAGES
Cybercriminals and nation state-sponsored spies didn't take long to catch onto the coronavirus panic. Research released Thursday shows crooks and snoops have been rapidly registering vast numbers of potentially-malicious websites and sending out masses of scam emails as they try to make money from the pandemic.
A report from cybersecurity company Recorded Future noted a significant rise in website registrations related to the COVID-19 virus, some of which it believes are being used to either pilfer information from recipients or infect them with malware.
Lindsay Kaye, director of operation outcomes at Recorded Future, specifically called out the following domains as potentially dangerous:
- coronavirusstatus[.]space
- coronavirus-map[.]com
- blogcoronacl.canalcero[.]digital
- coronavirus[.]zone
- coronavirus-realtime[.]com
- coronavirus[.]app
- bgvfr.coronavirusaware[.]xyz
- coronavirusaware[.]xyz
Forbes also had Bernardo Quintero, founder of the Google-owned malware repository and anti-virus testing service VirusTotal, take a look at the domains reported by Recorded Future. He said the following websites also showed signs of malicious behavior, as they’re being detected by anti-virus software:
Today In: Cybersecurity
- corona-virus[.]healthcare
- survivecoronavirus[.]org
- vaccine-coronavirus[.]com
- coronavirus[.]cc
- bestcoronavirusprotect[.]tk
- coronavirusupdate[.]tk
A significant number of additional coronavirus-related domains have been registered in recent days, and whilst they hadn’t yet been linked to criminal activity, they may do in the coming weeks, said Kaye.
There are, for instance, domains registered that appear to come from the Centers for Disease Control and Prevention (CDC), when in fact they’re from dangerous spammers. Researchers have already found one malware that was spread via the legitimate-looking email address CDC-Covid19@cdc[.]gov. And, as previously reported, there is at least one malicious coronavirus map that secretly installs malware that can steal information from victim PCs.
“It is advisable to treat all emails regarding the COVID-19 outbreak with caution,” wrote Recorded Future.
Phishing email examples
Cybersecurity company FireEye provided Forbes with a handful of example spam emails. Often such scams will ask you to click on a link or attachment so that you can get more information about protecting yourself from coronavirus.
Again, if you see anything that looks like they following, it’s wise to close and delete the email, and not click on links or attachments.

A criminal phishing email seeking to take advantage of the coronavirus pandemic.
FIREEYE

Another malicious phishing email seeking to take advantage of the coronavirus panic.
FIREEYE
FireEye also looked at some of the attachments being sent in COVID-19 phishing emails. If you’ve downloaded something similar to this, run your antivirus and any other security tools that can help you check for infection.

A "lure" document that FireEye believes a Chinese group of hackers used to try to infect targets in ... [+]
FIREEYE
Government spies are taking advantage of coronavirus
It’s not just opportunistic scammers who’re making the most out of coronavirus. Espionage groups associated with China, North Korea and Russia have been seen sending out spear phishing emails trying to find routes onto business networks.
Entire industries are being targeted. In February, cybersecurity company Proofpoint noted Coronavirus-themed email attacks tried to play on concerns about disruptions to global shipping. The hackers behind the operation were “exclusively targeting industries that are particularly susceptible to shipping disruptions including manufacturing, industrial, finance, transportation, pharmaceutical, and cosmetic companies.”
In late February and early March, FireEye suspected a group of Chinese hackers had sent malware-laden documents to targets in Vietnam, the Philippines and Taiwan.
The documents included legitimate statements by political leaders and advice from official sources, but hidden underneath was data-slurping spyware. As reported by ForbesThursday, a Chinese hacking crew has been linked to coronavirus-led attacks on Mongolians.
FireEye also reported that an espionage group called TEMP.Armageddon, which “acts in support of Russian interests,” sent a spear phishing email with a malicious, coronavirus-themed document to Ukrainians. And the company’s researchers said they’d seen South Korea NGO targeted with a Korean-language lure entitled “Coronavirus Correspondence.” Though they’re still probing the attack, the analysts have already noted some similarities to previously-seen North Korean hacks.
If you’re a potential target for cybercrime or international spies - which means you are a human being who uses the internet - be careful with what emails are trying to stoke the fire of your coronavirus fears.
