Fake Occupy Central app targets activists’ smartphones
PUBLISHED : Wednesday, 17 September, 2014, 5:12pm
UPDATED : Wednesday, 17 September, 2014, 9:38pm
Patrick Boehler and Cedric Sam

Protestors hold Black Cloth match to Chater Road from Causeway Bay during Occupy Central with Love and Peace conduct a "Black Cloth March" on Sunday. Photo: Felix Wong
A fraudulent smartphone app claiming to coordinate the Occupy Central pro-democracy movement has circulated online, a group of programmers said on Wednesday.
The spyware is disguised as an application for Android smartphones or tablets, Code4HK, a group of coders trying to improve government transparency in Hong Kong, said.
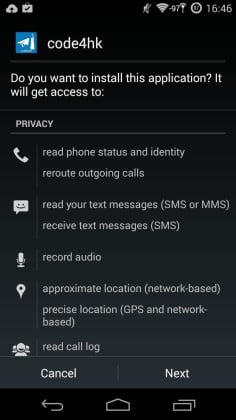
A screenshot of the information requested by the application.
Activists first received a link to the application in messages from a phone number unknown to them on Tuesday. “Check out this Android app designed by Code4HK for the coordination of Occupy Central!” the message read.
Lau Sau-yin, a spokeswoman for Occupy Central, said the organisation had nothing to do with the spyware. Code4HK also said that none of its members developed or distributed the application. “None of the Code4HK community has done any application on [Occupy Central] at the moment nor sent the message,” the statement read.
The number that shared the software could not be reached on Wednesday.
Once downloaded and installed the application requests access to information on users’ contacts, browsing history, approximate location, text messages, and phone call history.
Siu Cheong Leung, a senior consultant with the Hong Kong Computer Emergency Response Team Coordination Centre, said suspicious behaviour by the application included recording audio and obtaining the location of the device. "It's a malware with spy behaviour," he said.
"On the face it is not suspicious," he added. "However once it is installed, it will unpack data from itself to install a second mobile app," which then connects to a server based in South Korea.
Code4HK suggested the application was generic spyware. “I agree it looks quite off the shelf, not specialised for us,” said Vincent Lau Chun-yin, a member of the group.
The group of coders was not able to immediately identify the origin of the spyware. The server hosting the application has a log-in in simplified Chinese predominantly used on the mainland.
